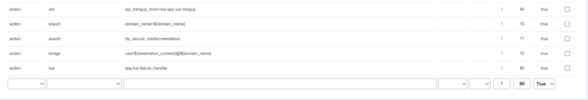
Hey Everyone,
I am running on FusionxPBX 5.3.8.
I have enabled TLS and SRTP.
I have a Yealink and a Grandstream phone for testing. Both set to Mandatory SRTP.
When I make outbound calls from either handset, I get valid encryption: AES_CM_128_HMAC_SHA1_80 from the Yealink and AEAD_AES_256_GCM from the Grandstream.
Incoming I get AES_CM_128_HMAC_SHA1_80 to the Yealink and both AES_CM_128_HMAC_SHA1_80 and AEAD_AES_256_GCM to the Grandstream.
I think that part is fine and working correctly.
My issue is with internal calling.
When I call from either one, the calls go straight to voicemail. I get INCOMPATIBLE_DESTINATION error in the CDR for the call. I am assuming it is one phone is using one encryption cipher and the other is using a different cipher, and they don't negotiate.
If I set SRTP to Optional on the Grandstream, I can call the Yealink phone due to no SRTP being used. If I set the Yealink to Optional, it still fails.
Is there something I am missing? Or is it just an issue because of the different manufacturers?
Thanks for the help.
I am running on FusionxPBX 5.3.8.
I have enabled TLS and SRTP.
I have a Yealink and a Grandstream phone for testing. Both set to Mandatory SRTP.
When I make outbound calls from either handset, I get valid encryption: AES_CM_128_HMAC_SHA1_80 from the Yealink and AEAD_AES_256_GCM from the Grandstream.
Incoming I get AES_CM_128_HMAC_SHA1_80 to the Yealink and both AES_CM_128_HMAC_SHA1_80 and AEAD_AES_256_GCM to the Grandstream.
I think that part is fine and working correctly.
My issue is with internal calling.
When I call from either one, the calls go straight to voicemail. I get INCOMPATIBLE_DESTINATION error in the CDR for the call. I am assuming it is one phone is using one encryption cipher and the other is using a different cipher, and they don't negotiate.
If I set SRTP to Optional on the Grandstream, I can call the Yealink phone due to no SRTP being used. If I set the Yealink to Optional, it still fails.
Is there something I am missing? Or is it just an issue because of the different manufacturers?
Thanks for the help.