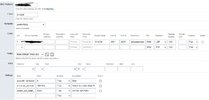
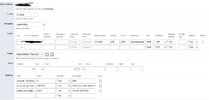
In the device settings, you have the choice to set up your device as UDP or TCP. I am assuming you use port 5080 regardless
Now I was told that some of the natting issues I was having would actually benefit by using TCP rather than UDP
Can anyone shed light on this? Does TCP really offer a better path for nat than UDP?
In addition, there were port conflicts from time to time (sip listen ports). So, I assigned a specific port to each yealink T29G in the building
5062, 5064, 5066, 5068 and so on........
this did help with the random drops, but I am trying to fine tune and ensure a rock solid set up. I am currently using UDP
See attached image for my device set up
Any insight, suggestions, ideas are welcomed
Now I was told that some of the natting issues I was having would actually benefit by using TCP rather than UDP
Can anyone shed light on this? Does TCP really offer a better path for nat than UDP?
In addition, there were port conflicts from time to time (sip listen ports). So, I assigned a specific port to each yealink T29G in the building
5062, 5064, 5066, 5068 and so on........
this did help with the random drops, but I am trying to fine tune and ensure a rock solid set up. I am currently using UDP
See attached image for my device set up
Any insight, suggestions, ideas are welcomed